Why Proactive IT Monitoring is a Game Changer for Dallas-Fort Worth Businesses
In today’s digital world, small and midsize businesses across Dallas, Fort Worth, Frisco, Plano, and Arlington depend on technology for every aspect...

Introduction
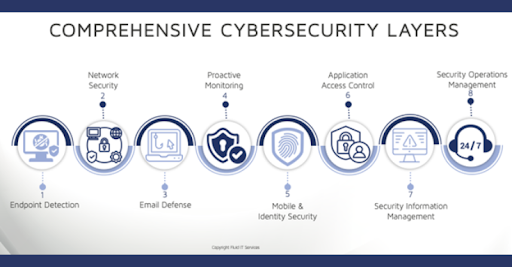
Most business owners understand they need antivirus software, but endpoint security goes far deeper than that. Every laptop, desktop, tablet, and smartphone connected to your network is a potential entry point for cybercriminals. A single compromised device can bring your entire operation to a halt.
Your Weakest Link is Mobile
Remote work has expanded your attack surface exponentially. Employees accessing company data from coffee shops, home networks, and airports create vulnerabilities that traditional perimeter security can't address. Endpoint Detection and Response (EDR) tools provide real-time monitoring and threat hunting across all devices, wherever they are.
Beyond Antivirus: A Layered Approach
Modern endpoint security combines multiple defensive layers. Antivirus is just the foundation. You also need patch management to close software vulnerabilities, application whitelisting to prevent unauthorized programs, and device encryption to protect data if a laptop is lost or stolen.
Key Protection Measures:
• Automated Patch Management: Eliminates vulnerabilities before they're exploited.
• Multi-Factor Authentication: Stops credential theft attacks in their tracks.
• Device Encryption: Protects sensitive data even if hardware is compromised.
• 24/7 Monitoring: Catches threats outside business hours when attacks often occur.
Conclusion
A data breach doesn't just cost money—it damages reputation and client trust. Comprehensive endpoint security isn't optional anymore; it's the baseline for doing business safely in a connected world.

In today’s digital world, small and midsize businesses across Dallas, Fort Worth, Frisco, Plano, and Arlington depend on technology for every aspect...

The Need for Constant Communication How do business leaders make decisions regarding IT? Do they have a formal process, or is it informal word of...
XSP Defined Cybersecurity is the predominant concern of both small and large businesses. Therefore, securityis a top priority for Fluid IT and all...