Bridging the IT Gap: Simplifying MSP and MSSP Services
MSP and MSSP Services Simplified One of the biggest challenges in my field—and it seems to be getting worse—is how tech companies, vendors, and...
Cybersecurity is the predominant concern of both small and large businesses. Therefore, security
is a top priority for Fluid IT and all our clients. What many business owners, managers, and
employees don’t know, however, is all that happens behind the scenes. Unfortunately, security
only seems to become paramount when there is an incident, a pain point that impacts the
business and diverts it from its core objectives.
To peek behind the curtain, you would see that cybersecurity requires a continual, never-ending
review and improvement process. Most times, Fluid’s security capabilities go unnoticed by the
end user; this is our unending goal: no disruption to user productivity. Although rare, there are
instances where we feel additional communication is warranted, even though the business and
end-user are not impacted.
One of the most frustrating aspects of my job and my industry that hasn’t changed and one could
argue has become worse is that technology companies, vendors, and service providers speak in
technology terms and countless acronyms, forcing the business community to figure it out. This
truth is not just saved for deep technical discussions but exists at the highest level of IT. Case in
point: What we do is now called managed services, most commonly called MSP (Managed
Service Provider) services.
While we continually adapt our technology capabilities, services, and solutions to provide best-
in-class services to our clients, what we do in principle has been the same over the past twenty
years.
We provide comprehensive technology services, solutions, and advisory services to cover the
entire technology spectrum for businesses that cannot or should not hire internal IT staff. Our
services include helpdesk support, software application support, cloud services, virtual CIO
(oops, I just threw another acronym out there–Chief Information Officer), experienced senior-
level business technology advisory services, and cybersecurity.
As the years have passed, the importance of cybersecurity has continued to rise in the
consciousness of businesses as the damage and actual costs have increased to the point that one
bad event can put you out of business. Cybersecurity has forced itself into the discussion of the
board members and not only the IT budget; it is now the number one concern of business owners
and management, creating the need for its own budget.

Yet another new acronym appeared during this time: MSSP, or Managed Security Solution
Provider. The general idea is that an MSSP focuses on providing cybersecurity solutions and
services, while an MSP only focuses on general comprehensive IT services. The inference is that
MSPs do not and cannot provide adequate cybersecurity services and solutions, resulting in the
need to create an entirely new business offering–MSSPs–to address this gap.
Searching for MSPs and a second search for MSSPs will result in two different results. The
irritating aspect of this development is that it adds more confusion not only to the technology
services market but also to the business community and non-technical buyers of services.
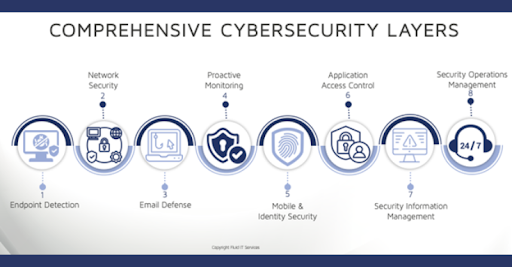
We have divided and defined cybersecurity into eight layers to alleviate the confusion. Put
another way; we have eight different security blankets to address additive security measures for
businesses regardless of size and industry. We have taken the best of the traditional cybersecurity
services and solutions and layered four more advanced cybersecurity solutions and services.

Fluid has continually improved security services and solutions for our clients over the years, and,
more recently, we have aggressively added more advanced capabilities that MSSPs state only
they can offer.
In light of the security landscape, our only logical choice was to expand our offerings to include
advanced cybersecurity solutions and services in a single offering we call XSP or Extended
Service Provider. While this is not a unique term, it does attempt to address the merging of the
traditional MSP and more advanced cybersecurity MSSP services.
A forward-thinking, high-value managed service provider should provide/offer many, if not all,
of the cybersecurity services MSSPs provide. We should be at the point where top MSPs can and
do provide comprehensive cybersecurity services and solutions that prevent the need to add yet
another vendor to the mix to pay for and manage. There will always be very specific and targeted
solutions that will be and often should remain separate, such as penetration testing and forensics.
As the illustration shows, Fluid has added four additional layers of advanced cybersecurity
solutions to provide a comprehensive menu for businesses based on their increasing
cybersecurity needs.

Specifically, Fluid has added four additional layers of cybersecurity:
1. Mobile Devices and Identity Management
2. Application Access Control
3. Security Information and Event Management (SIEM)
4. Security Operations Center (SOC)
The additional four layers of security are differentiated from the norm in what we describe as
‘eyes on screens,’ meaning they require physical staff monitoring and remediating issues
24/7/365. Specifically, at levels seven and eight, no level of automation or AI can replace human
analysis, review, and problem-solving.
Fluid now offers these advanced levels of security to our current and future clients. In the coming
blogs, I will dive into deeper details of the additional levels four through eight.
.jpg)
MSP and MSSP Services Simplified One of the biggest challenges in my field—and it seems to be getting worse—is how tech companies, vendors, and...
Hiring an in-house IT professional offers a few key benefits. However, this approach comes with significant drawbacks, especially for a new or small...
Hiring senior leaders is expensive. The fastest way to help them deliver value is to make day one frictionless and week one productive. A mature IT...